Linux is an incredibly powerful and versatile operating system, and one of its core features is the permissions. Understanding how linux permissions work is crucial for anyone working with Linux, whether you’re a system administrator, developer, or a casual user. In this blog post, we will delve deep into the world of Linux permissions, covering the basics as well as some more advanced topics. So, let’s get started!
Table of Contents
Basics of Linux permissions
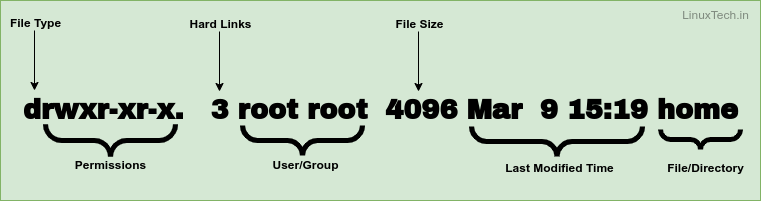
Users and groups
In Linux, each user is associated with a unique user ID (UID) and belongs to one or more groups, each with a unique group ID (GID). Users can be regular users, system users, or the superuser (root). Groups help in managing multiple users with similar access requirements.
To create a new user and group, you can use the following commands:
sudo useradd -m newuser
sudo passwd newuser
sudo groupadd newgroup
sudo usermod -a -G newgroup newuser
File permissions
File permissions determine the actions users and groups can perform on a file. There are three types of permissions: read (r), write (w), and execute (x). Read permission allows viewing the file content, write permission enables modifying the file, and execute permission allows running the file as a program or script.
Consider a file called file.txt with the following permissions:
-rw-r--r--. 1 root root 1032 Jan 2 16:12 file.txt
The owner has read and write permissions, while the group and others have read permissions.
Directory permissions
Directory permissions control access to directories and their content. Similar to file permissions, there are read (r), write (w), and execute (x) permissions for directories. Read permission allows listing directory content, write permission allows creating or deleting files and subdirectories, and execute permission allows accessing files and subdirectories within the directory.
Consider a directory called my_directory with the following permissions:
drwxr-xr-x. 2 root root 4096 Jan 2 16:45 my_directory
The owner has read, write, and execute permissions, while the group and others have read and execute permissions.
Understanding permission notation
Symbolic notation
In symbolic notation, permissions are represented by a string of characters. The first character denotes the file type (e.g., ‘-‘ for regular files, ‘d’ for directories). The next nine characters are grouped into three sets, representing the owner, group, and others’ permissions, respectively. Each set has three characters, corresponding to read (r), write (w), and execute (x) permissions. For example, the notation ‘-rw-r–r–‘ represents a regular file with read and write permissions for the owner and read permissions for the group and others.
A symbolic notation for a file with read and write permissions for the owner and read permissions for the group and others is:
-rw-r--r--
Numeric (octal) notation
In numeric notation, permissions are represented by a three-digit number, with each digit ranging from 0 to 7. Each digit corresponds to the owner, group, and others’ permissions. The digit’s value is calculated by adding the values assigned to each permission: 4 for read (r), 2 for write (w), and 1 for execute (x). For example, the numeric notation 644 represents read and write permissions for the owner and read permissions for the group and others.
The equivalent numeric notation for the same file mentioned above is:
644
Manipulating permissions
chmod command
The chmod command is used to modify file and directory permissions. It accepts both symbolic and numeric notations.
To add execute permissions for the group on a file named script.sh, use:
chmod g+x script.sh
To add read, write, and execute permissions for the owner, and read and execute permissions for the group and others on a directory named my_direcroty, use:
chmod 755 my_direcroty
chown command
The chown command is used to change the owner of a file or directory.
To change the owner of a file named file.txt to ‘newuser’, use:
sudo chown newuser file.txt
chgrp command
The chgrp command is used to change the group ownership of a file or directory.
To change the group ownership of a file named file.txt to ‘newgroup’, use:
sudo chgrp newgroup file.txt
Special permissions
Setuid
The setuid (set user ID) permission, when applied to an executable file, allows the file to be executed with the privileges of the file owner, rather than the user executing the file. This is denoted by an ‘s’ in the owner’s execute position.
To set the setuid permission on a file named setuid_program, use:
sudo chmod u+s setuid_program
Setgid
The setgid (set group ID) permission, when applied to an executable file, allows the file to be executed with the privileges of the file’s group, rather than the user’s group. When applied to a directory, new files and directories created within will inherit the group ownership of the parent directory. This is denoted by an ‘s’ in the group’s execute position.
To set the setgid permission on a directory named shared_directory, use:
sudo chmod g+s shared_directory
Sticky bit
The sticky bit permission, when applied to a directory, restricts file deletion within that directory. Users can only delete files they own, even if they have write permission on the directory. This is denoted by a ‘t’ in the others’ execute position.
To set the sticky bit permission on a directory named public_directory, use:
sudo chmod o+t public_directory
Access control lists (ACLs)
ACLs provide more granular control over file and directory permissions by allowing you to set specific permissions for individual users and groups. The getfacl and setfacl commands are used to view and modify ACLs, respectively.
To grant read and write permissions on a file named file.txt to user ‘otheruser’, use:
setfacl -m u:otheruser:rw file.txt
Best practices and recommendations
Follow the principle of least privilege: Grant users and applications the minimum necessary permissions to perform their tasks.
Regularly review and update permissions as user roles and requirements change.
Avoid using overly permissive settings, such as 777, which grant all permissions to all users.
Use ACLs for fine-grained access control when required, but keep in mind their complexity and potential performance impact.
Keep the setuid, setgid, and sticky bit permissions to a minimum and only use them when absolutely necessary, as they can introduce security risks.
Conclusion
Linux permissions are a fundamental part of the operating system, ensuring security and proper access control. By understanding the different types of permissions, how they are represented, and the commands used to manipulate them, you can effectively manage your Linux environment. Be mindful of best practices to maintain a secure and organized system.
Got any queries or feedback? Feel free to drop a comment below!

